Introduction
Hash Cryptography is one of the main pillars of any Blockchain. It is what makes blockchains what they are, a securely linked chain of blocks. And today, we’re going to learn why.
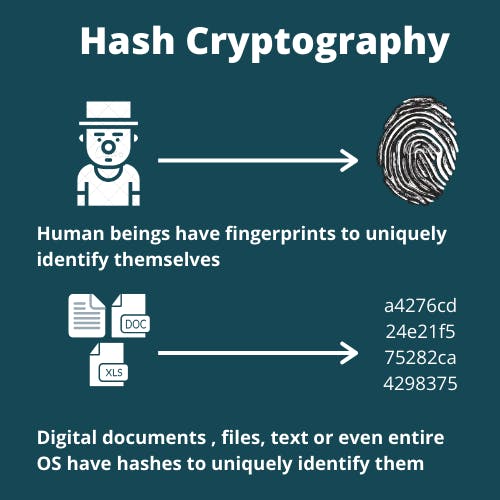
What is the easiest way for us to uniquely identify humans?
“Just by looking at them” is not the answer. There are too many people with the same hairstyle, similar facial structure, skin tone and almost all other visual factors.
I’m going to save you time, and tell you the answer. Fingerprint.

The easiest way to uniquely identify humans is by their fingerprints. Almost every human has a unique fingerprint. And this can be(and is) used to uniquely identify us.
What about digital documents? Or a piece of text? Or an audio file? Or an entire Operating System?! How to identify these uniquely?
The answer is same. Digital fingerprint.
Digital Documents
Hash Cryptography helps us find these digital fingerprints. You take a piece of information (could be a pdf, a text, or a movie), pass it through a cryptographic hash function and the output you will receive is the hash (or digital fingerprint) of that document.
In the previous post , we saw how the chain of blocks is linked using the Previous Hash field in the Bitcoin Blockchain. The Previous Hash and the Hash field are computed using a cryptographic hash function.
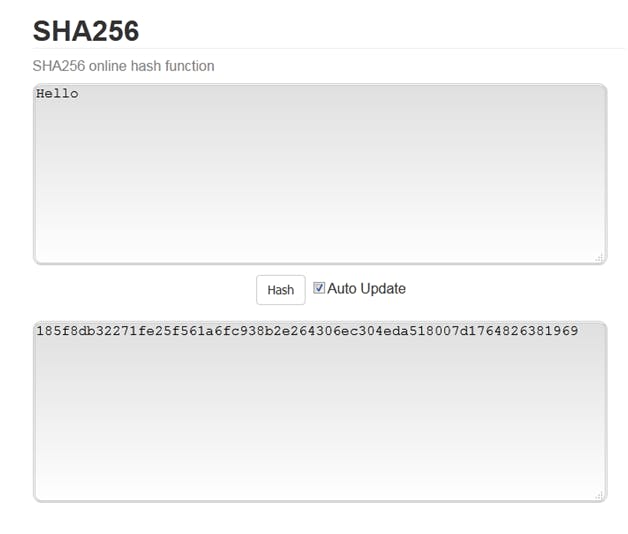
The cryptographic hash function used in this case is SHA256. SHA stands for Secure Hash Algorithm, a family of many cryptographic hash functions like SHA256, SHA512, SHA128, etc. SHA256 was developed by the NSA (National Security Agency) and the code was later made open source. The 256 in the name denotes the number of bits it takes in memory. It is a 64 character long hexadecimal hash where 4 bits represent each hexadecimal number.
Below is an example SHA256 hash of the input string "Hello"
Bitcoin Blockchain
In the Bitcoin Blockchain, the current hash is computed by giving the Data Field and the Previous Hash field as input to the SHA256 function, and the function returns the output i.e. the hash or fingerprint of the given data.
You can use the SHA256 or any modern cryptographic hash functions to find the hash (fingerprint) of any piece of information. You can find the hash value of documents, strings, executables, binaries, movies, entire operating systems, etc.
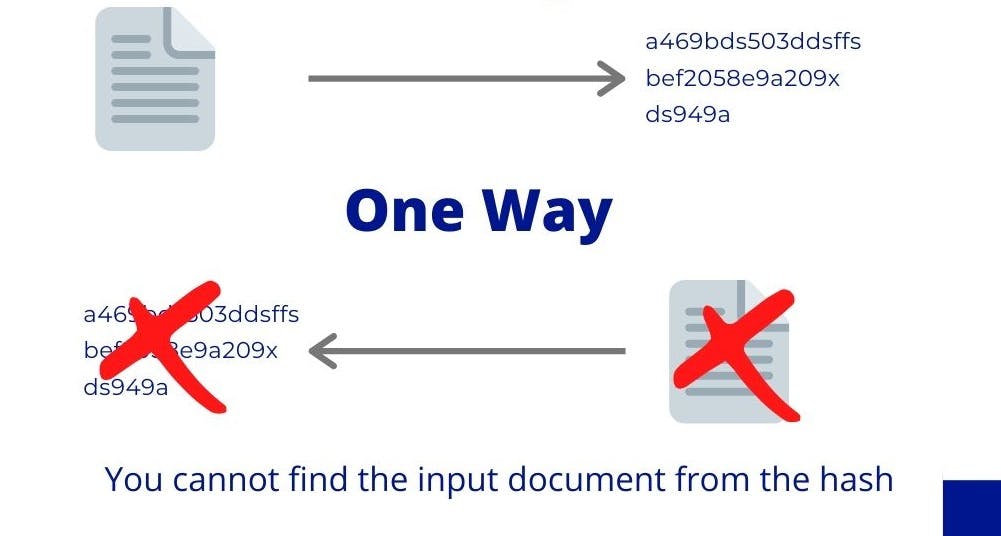
An important property of cryptographic hash functions is that they are one way. Which means, you can go from a document to finding its hash, but not the other way. You cannot recover a document from its hash. This is what makes hashes secure and protects the immutability of blockchains.
In addition to being one way, a good cryptographic hash function should have five important properties. We will cover these five properties in detail in the next post.
Until next time.
Feel free to reach out on Twitter(@ar6aaz ) or Instagram(@theblockchainblog )

