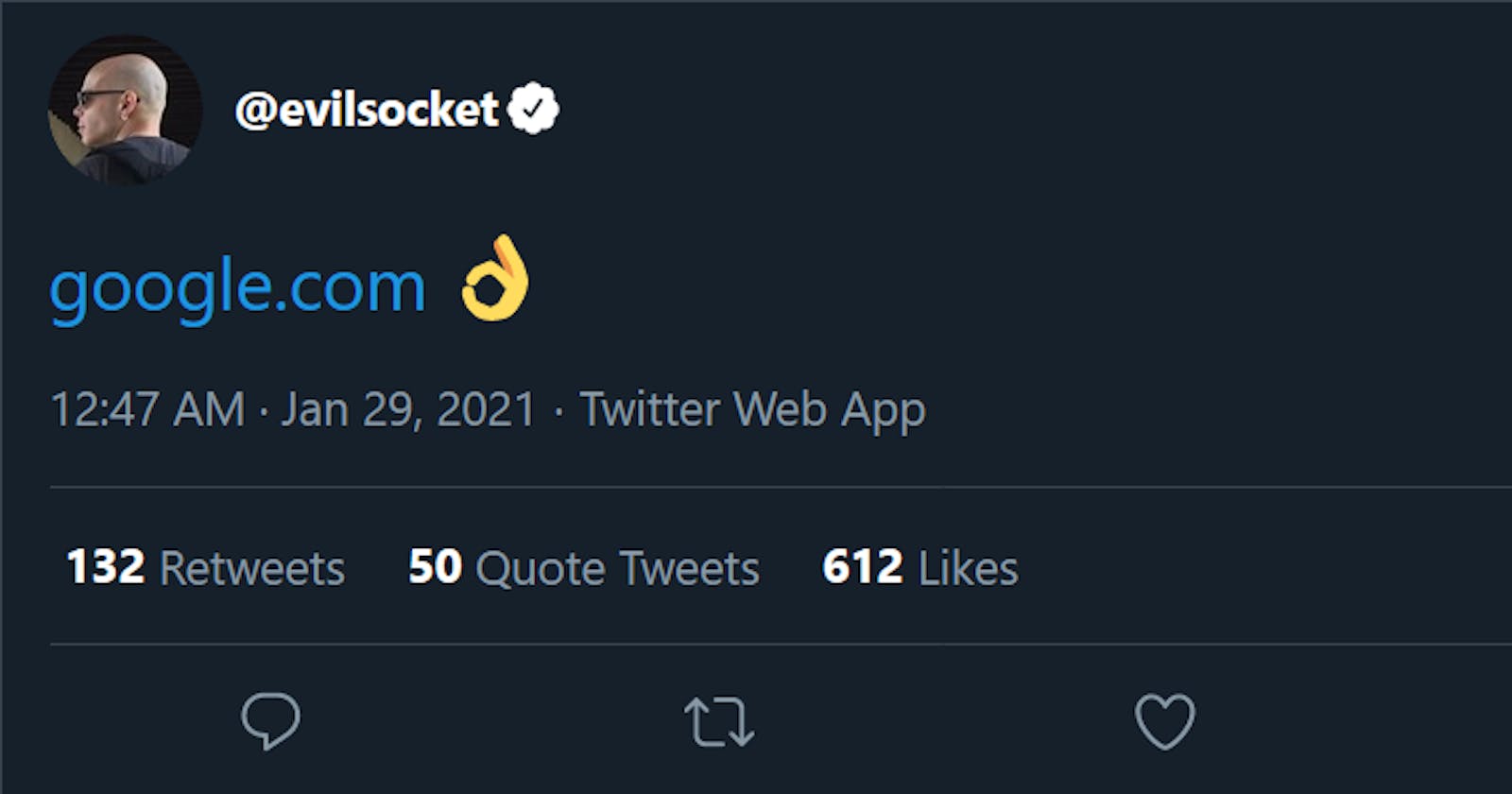
Yesterday, I came across an interesting tweet from Simone(@evilsocket on Twitter). In the tweet, he put a link to goᴏgle.com which on clicking, redirects to his Twitter account. Try it, click on the link in this tweet and see where you land up at. Weird, right?
The link looks legit, yet it takes you to his Twitter account. Did he just hack Google?
Not really. In order to understand what is happening here, we will need to first understand IDN homographs.
IDN
IDN stands for Internationalized Domain Names. It is a mechanism for handling domain names that contain characters other than normal ASCII characters. For example, domain names can contain Latin characters, Cyrillic characters, etc. But these International Domain Names can still not be represented in their Unicode format in URLs.
In comes Punycode. Punycode is a technique to represent these Unicode characters in their ASCII form. The corresponding ASCII code post Punycode conversion is in the form of hyphens, numbers and letters.
So let’s try to decode goᴏgle.com and see what its Punycode representation is. Head over to punycoder.com (Don’t worry, this is not a homograph link)
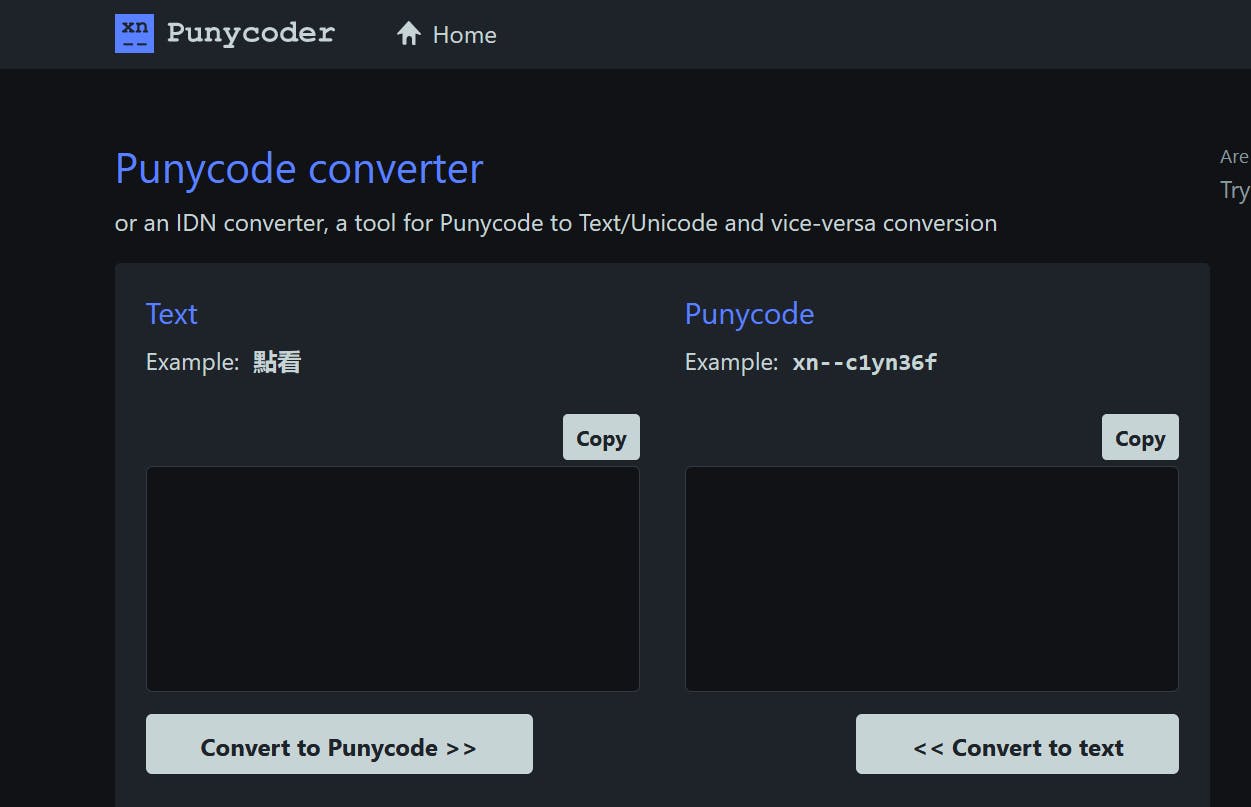
Next, paste the URL goᴏgle.com in the text box and click on ‘Convert to Punycode’.
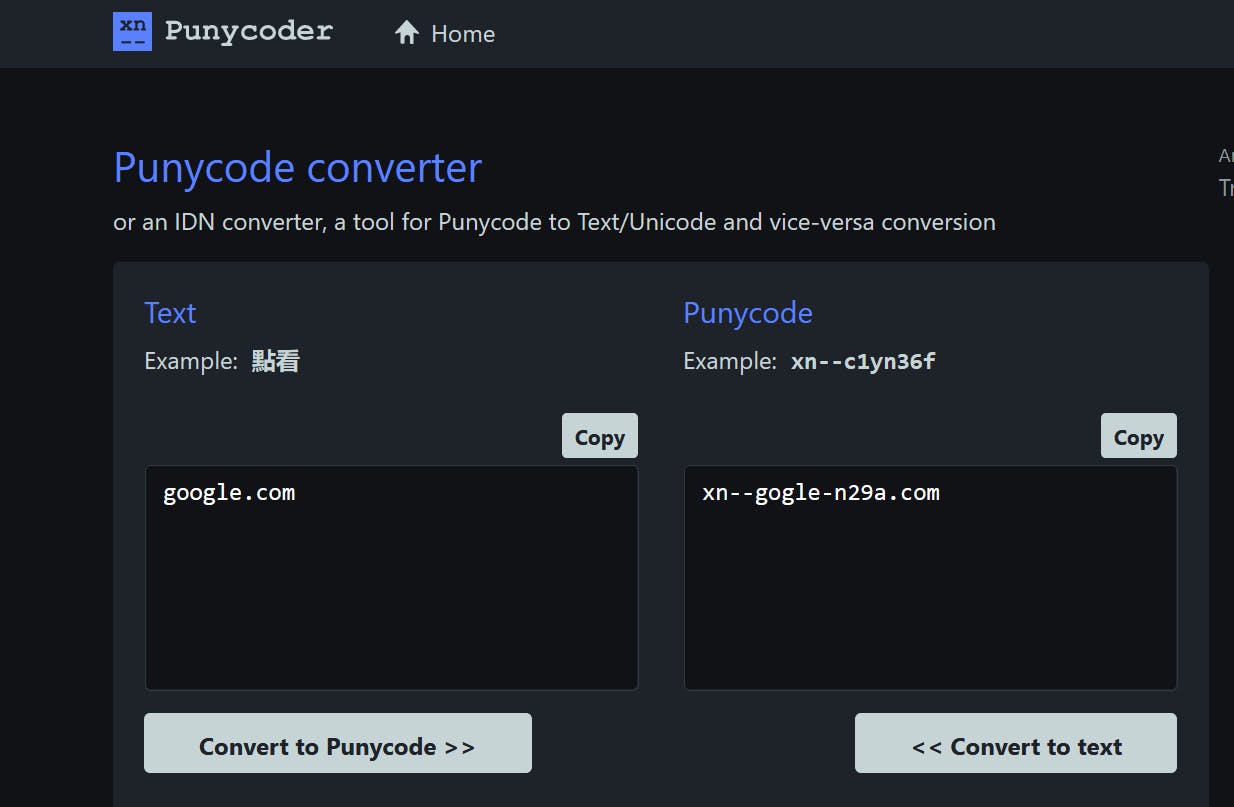
There it is, xn--gogle-n29a.com is the unmasked URL in Punycode format that was hiding behind the International Domain Name goᴏgle.com. So what Simone(@evilsocket) probably did, was he bought the domain xn--gogle-n29a.com and redirected all requests on the domain to his Twitter profile.
If you’re interested in knowing more about the ToASCII and ToUnicode functions that are used for the conversion, you can get more details on RFC3490 here .
Now comes the interesting part. How can an attacker leverage the use of IDN homographs?
Phishing
The first and obvious way is phishing. Majority of us would definitely click on the Google link from that tweet without hesitation. So imagine an attacker does this on an application that requires login. He can easily mass harvest credentials of users by creating an identical phishing page on the IDN homographed domain.
Another way would be using these domains to download and install malware on the computers of users who visit the site.
URL Redirects
URL redirection is another scenario where an attacker could use IDNs. For instance, let’s say we have an application target.com . The application has redirects that are accepted as valid only when the redirects are to the same origin target.com/*. An attacker can replace any of the letters in URL with Cyrillic characters. And if the server is not configured to convert the hostname to Punycode before validating the URL, it could redirect the user to the malicious URL.
Original URL: target.com/login?redirectURL:http://google...
Malicious URL: target.com/login?redirectURL:http://goᴏgle.com
The difference in the two URLs is not noticeable to the naked eye(here it is because hashnode is secure) but if a user clicks on the second URL, it will lead him to the malicious website. The attacker can potentially escalate the redirect to XSS if he can load and executes Javascript from the redirected URL.
Password Reset
IDNs can also be used on Password Reset functionality of applications to change password of any user. For example, let’s say arbaaz@gmail.com has an account on target.com. An attacker can send a password reset request for arbaaz@gmáil.com (notice the á).
If the password reset functionality is not configured to convert the email to Punycode and then validate it, it will send the password reset link to arbaaz@gmáil.com, i.e. xn--arbaaz@gmil-s7a.com in its ASCII converted form.
An attacker can buy the domain xn--arbaaz@gmil-s7a.com and get the credentials for arbaaz@gmail.com by requesting password reset on arbaaz@gmáil.com
So that is how IDN homographs work. I will leave you with this report where a security researcher was able to able to get a user’s OAuth token on SEMRush using IDN homographs.
For any questions, feel free to reach out on Twitter or Instagram
Until next time.